Industry forces — led by Apple and Google — are pushing for a sharp acceleration of how often website certificates must be updated, but the stated security reason is raising an awful lot of eyebrows.
Website certificates, also known as SSL/TLS certificates, use public-key cryptography to authenticate websites to web browsers. Issued by trusted certification authorities (CAs) that verify the ownership of web addresses, site certificates were originally valid for eight to ten years. That window dropped to five years in 2012 and has gradually stepped down to 398 days today.
The two leading browser makers, among others, have continued to advocate for a much faster update cadence. In 2023, Google called for site certificates that are valid for no more than 90 days, and in late 2024, Apple submitted a proposal to the Certification Authority Browser Forum (CA/Browser Forum) to have certificates expire in 47 days by March 15, 2028. (Different versions of the proposal have referenced 45 days, so it’s often referred to as the 45-day proposal.)
If the CA/Browser Forum adopts Apple’s proposal, IT departments that currently update their company’s site certificates once a year will have to do so approximately every six weeks, an eightfold increase. Even Google’s more modest 90-day proposal would multiply IT’s workload by four. Here’s what companies need to know to prepare.
The official reason for speeding up the certificate renewal cycle is to make it far harder for cyberthieves to leverage what are known as orphaned domain names to fuel phishing and other cons to steal data and credentials.
Orphaned domain names come about when an enterprise pays to reserve a variety of domain names and then forgets about them. For example, Nabisco might think up a bunch of names for cereals that it might launch next year — or Pfizer might do the same with various possible drug names — and then eight managerial meetings later, all but two of the names are discarded because those products will not be launching. How often does someone bother to relinquish those no-longer-needed domain names?
Even worse, most domain name registrars have no mechanism to surrender an already-paid-for name. The registrar just tells the company, “Make sure it’s not auto-renewed, and then don’t renew it later.”
When bad guys find those abandoned sites, they can grab them and try and use them for illegal purposes. Therefore, the argument goes, the shorter the timeframe when those site certificates are valid, the less of a security threat it poses. That is one of those arguments that seems entirely reasonable on a whiteboard, but it doesn’t reflect reality in the field.
Shortening the timeframe might lessen those attacks, but only if the timeframe is so short it denies the attackers sufficient time to do their evil. And, some security specialists argue, 47 days is still plenty of time. Therefore, those attacks are unlikely to be materially reduced.
“I don’t think it is going to solve the problem that they think is going to be solved — or at least that they have advertised it is going to solve,” said Jon Nelson, the principal advisory director for security and privacy at the Info-Tech Research Group. “Forty-seven days is a world of time for me as a bad guy to do whatever I want to do with that compromised certificate.”
Himanshu Anand, a researcher at security vendor c/side, agreed: “If a bad actor manages to get their hands on a script, they can still very likely find a buyer for it on the dark web over a period of 45 days.”
That is why Anand is advocating for even more frequent updates. “In seven days, the amount of coordination required to transfer and establish a worthy man-in-the-middle attack would make it a lot tighter and tougher for bad actors.”
But Nelson questions whether expired domain stealing is even a material concern for enterprises today.
“Of all of the people I talk with, I don’t think I have talked with a single one that has had an incident dealing with a compromised certificate,” Nelson said. “This isn’t one of the top ten problems that needs to be solved.”
That opinion is shared by Alex Lanstein, the CTO of security vendor StrikeReady. “I don’t want to say that this is a solution in search of a problem, but abusing website certs — this is a rare problem,” Lanstein said. “The number of times when an attacker has stolen a cert and used it to impersonate a stolen domain” is small.
Nevertheless, it seems clear that sharply accelerated certificate expiration dates are coming. And that will place a dramatically larger burden on IT departments and almost certainly force them to adopt automation. Indeed, Nelson argues that it’s mostly an effort for vendors to make money by selling their automation tools.
“It’s a cash grab by those tool makers to force people to buy their technology. [IT departments] can handle their PKI [Public Key Infrastructure] internally, and it’s not an especially heavy lift,” Nelson said.
But it becomes a much bigger burden when it has to be done every few months or weeks. In a nutshell, renewing a certificate manually requires the site owner to acquire the updated certificate data from the certification authority and transmit it to the hosting company, but the exact process varies depending on the CA, the specific level of certificate purchased, the rules of the hosting/cloud environment, the location of the host, and numerous other variables. The number of certificates an enterprise must renew ranges widely depending on the nature of the business and other circumstances.
C/side’s Anand predicted that a 45-day update cycle will prove to be “enough of a pain for IT to move away from legacy — read: manual — methods of handling scripts, which would allow for faster handling in the future.”
Automation can either be handled by third parties such as certificate lifecycle management (CLM) vendors, many of which are also CAs and members of the CA/Browser Forum, or it can be created in-house. The third-party approach can be configured numerous ways, but many involve granting that vendor some level of privileged access to enterprise systems — which is something that can be unnerving following the summer 2024 CrowdStrike situation, when a software update by the vendor brought down 8.5 million Windows PCs around the world. Still, that was an extreme example, given that CrowdStrike had access to the most sensitive area of any system: the kernel.
The $12 billion publisher Hearst is likely going to deal with the certificate change by allowing some external automation, but the company will build virtual fences around the automation software to maintain strict control, said Hearst CIO Atti Riazi.
“Larger, more mature organizations have the luxury of resources to place controls around these external entities. And so there can be a more sensible approach to the issue of how much unchecked automation is to exist, along with how much access the third parties are given,” Riazi said. “There will most likely be a proxy model that can be built where a middle ground is accessed from the outside, but the true endpoints are untouched by third parties.”
The certificate problem is not all that different from other technology challenges, she added.
“The issue exemplifies the reality of dealing with risk versus benefit. Organizational maturity, size, and security posture will play great roles in this issue. But the reality of certificates is not going away anytime soon,” Riazi said. “That is similar to saying we should all be at a passwordless stage by this point, but how many entities are truly passwordless yet?
There is a partially misleading term often used when discussing certificate expiration. When a site certificate expires, the public-facing part of the site doesn’t literally crash. To the site owner, it can feel like a crash, but it isn’t.
What happens is that there is an immediate plunge in traffic. Some visitors — depending on the security settings of their employer — may be fully blocked from visiting a site that has an expired certificate. For most visitors, though, their browser will simply flag that the certificate has expired and warn them that it’s dangerous to proceed without actually blocking them.
But Tim Callan, chief compliance officer at CLM vendor Sectigo and vice chair elect of the CA/Browser Forum, argues that site visitors “almost never navigate past the roadblock. It’s very foreboding.”
That said, an expired certificate can sometimes deliver true outages, because the certificate is also powering internal server-to-server interactions.
“The majority of certs are not powering human-facing websites; they are indeed powering those server-to-server interactions,” Callan said. “Most of the time, that is what the outage really is: systems stop.” In the worst scenarios, “server A stops talking to server B and you have a cascading failure.”
Either way, an expired certificate means that most site visitors won’t get to the site, so keeping certificates up to date is crucial. With a faster update cadence on the horizon, the time to make new plans for maintaining certificates is now.
All that said, IT departments may have some breathing room. StrikeReady’s Lanstein thinks the certification changes may not come as quickly or be as extreme as those outlined in Apple’s recent proposal.
“There is zero chance the 45 days will happen” by 2028, he said. “Google has been threatening to do the six-month thing for like five years. They will preannounce that they’re going to do something, and then in 2026, I guarantee that they will delay it. Not indefinitely, though.”
C/side’s Anand also noted that, for many enterprises, the certificate-maintenance process is multiple steps removed.
“Most modern public-facing platforms operate behind proxies such as Cloudflare, Fastly, or Akamai, or use front-end hosting providers like Netlify, Firebase, and Shopify,” Anand said. “Alternatively, many host on cloud platforms like AWS [Amazon Web Services], [Microsoft] Azure, or GCP [Google Cloud Platform], all of which offer automated certificate management. As a result, modern solutions significantly reduce or eliminate the manual effort required by IT teams.”
 Sen. Maria Cantwell, D-Wash., said Tuesday that Verizon and AT&T are preventing the release of documents tied to Salt Typhoon, a Chinese cyber collective that infiltrated U.S. telecom networks and other communications systems around the world.
Sen. Maria Cantwell, D-Wash., said Tuesday that Verizon and AT&T are preventing the release of documents tied to Salt Typhoon, a Chinese cyber collective that infiltrated U.S. telecom networks and other communications systems around the world. If you find yourself on one of these malicious websites and do not detect the threat quickly enough, you risk losing accounts, credentials and data. This is worse when it comes to Chrome or Safari on your phone, where spotting threats is harder.
If you find yourself on one of these malicious websites and do not detect the threat quickly enough, you risk losing accounts, credentials and data. This is worse when it comes to Chrome or Safari on your phone, where spotting threats is harder. Proton Mail, an encrypted email messaging service, allegedly disabled the accounts of two journalists investigating cybersecurity breaches in the South Korean government.
Proton Mail, an encrypted email messaging service, allegedly disabled the accounts of two journalists investigating cybersecurity breaches in the South Korean government. Starting on Monday night, users began reporting a mass outage at the 4chan.org domain, which has persisted for the last 12 hours, according to Downdetector.com.
Starting on Monday night, users began reporting a mass outage at the 4chan.org domain, which has persisted for the last 12 hours, according to Downdetector.com.  Cybersecurity researchers are warning of a new type of supply chain attack, Slopsquatting, induced by a hallucinating generative AI model recommending non-existent dependencies.
Cybersecurity researchers are warning of a new type of supply chain attack, Slopsquatting, induced by a hallucinating generative AI model recommending non-existent dependencies. Oracle has continued to downplay a data breach it suffered earlier this year, insisting in an email sent to customers this week that the hack did not involve its core platform, Oracle Cloud Infrastructure (OCI).
Oracle has continued to downplay a data breach it suffered earlier this year, insisting in an email sent to customers this week that the hack did not involve its core platform, Oracle Cloud Infrastructure (OCI). Following the compromise of a popular GitHub tool, developers having to turn and face their code repo’s strange ch-ch-changes.
Following the compromise of a popular GitHub tool, developers having to turn and face their code repo’s strange ch-ch-changes. Europe is scrambling to help Ukraine find a viable replacement for Elon Musk’s Starlink and our of Europe’s largest satellite companies are in talks with European leaders about how to shore up internet connectivity in Ukraine: France’s Eutelsat, Luxembourg’s SES, Spain’s Hisdesat, and Viasat, owner of the UK firm Inmarsat.
Europe is scrambling to help Ukraine find a viable replacement for Elon Musk’s Starlink and our of Europe’s largest satellite companies are in talks with European leaders about how to shore up internet connectivity in Ukraine: France’s Eutelsat, Luxembourg’s SES, Spain’s Hisdesat, and Viasat, owner of the UK firm Inmarsat. Google will soon begin testing a machine learning-based model that can estimate a user's age—or at least whether they're under 18, "so that we can apply protections to help provide more age-appropriate experiences."(More details:
Google will soon begin testing a machine learning-based model that can estimate a user's age—or at least whether they're under 18, "so that we can apply protections to help provide more age-appropriate experiences."(More details:  Industry forces — led by Apple and Google — are pushing for a sharp acceleration of how often website certificates must be updated, but the stated security reason is raising an awful lot of eyebrows.
Industry forces — led by Apple and Google — are pushing for a sharp acceleration of how often website certificates must be updated, but the stated security reason is raising an awful lot of eyebrows. Russia has reportedly cut some regions of the country off from the rest of the world's internet for a day, effectively siloing them, according to reports from European and Russian news outlets reshared by the US nonprofit Institute for the Study of War (ISW) and Western news outlets.
Russia has reportedly cut some regions of the country off from the rest of the world's internet for a day, effectively siloing them, according to reports from European and Russian news outlets reshared by the US nonprofit Institute for the Study of War (ISW) and Western news outlets.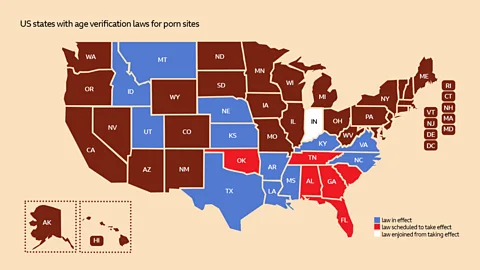 Pornhub is now blocked in Alabama amid a battle over the states' age-verification laws. It joins Arkansas, Indiana, Kentucky, Mississippi, Montana, North Carolina, Texas, Utah, Virginia, and Utah, where the adult site is also blocked—unless you try to get around it with a VPN. It's also poised to happen in Florida, where an age-verification law goes into effect on Jan. 1, 2025.
Pornhub is now blocked in Alabama amid a battle over the states' age-verification laws. It joins Arkansas, Indiana, Kentucky, Mississippi, Montana, North Carolina, Texas, Utah, Virginia, and Utah, where the adult site is also blocked—unless you try to get around it with a VPN. It's also poised to happen in Florida, where an age-verification law goes into effect on Jan. 1, 2025. A Telegram-based bot service has been collecting compromised credentials from accounts associated with the Democratic Party ahead of the Democratic National Convention later this month, according to a report released on Wednesday by ZeroFox.
A Telegram-based bot service has been collecting compromised credentials from accounts associated with the Democratic Party ahead of the Democratic National Convention later this month, according to a report released on Wednesday by ZeroFox.